|
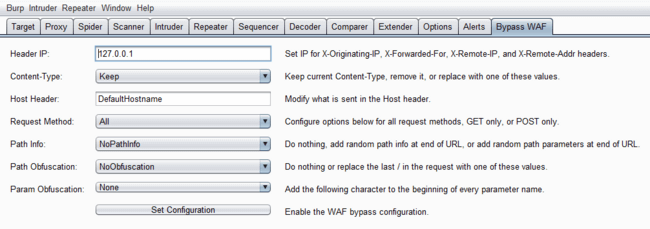
CDK |
| Make security testing of K8s, Docker, and Containerd easier. |
|
|
 |
jsfinder |
| Fetches JavaScript files quickly and comprehensively from a defined list of URLs or domains. |
|
|
 |
EAPHammer |
| Targeted attacks against WPA2-Enterprise networks, wireless pivots using hostile portal attacks. |
|
|
 |
katoolin3 |
| Get your favourite Kali Linux tools on Debian/Ubuntu/Linux Mint. |
|
|
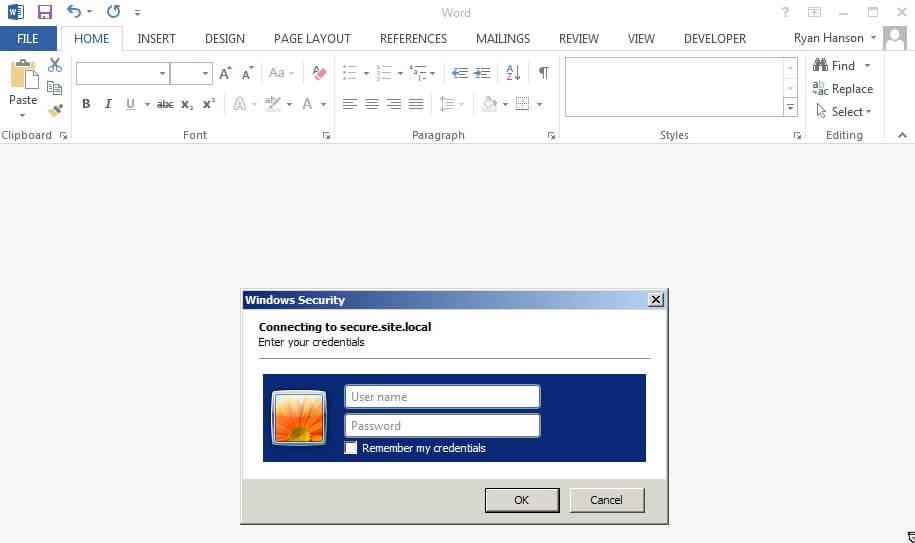 |
Phishery |
| An SSL enabled basic auth credential harvester with a Word document template URL injector. |
|
|
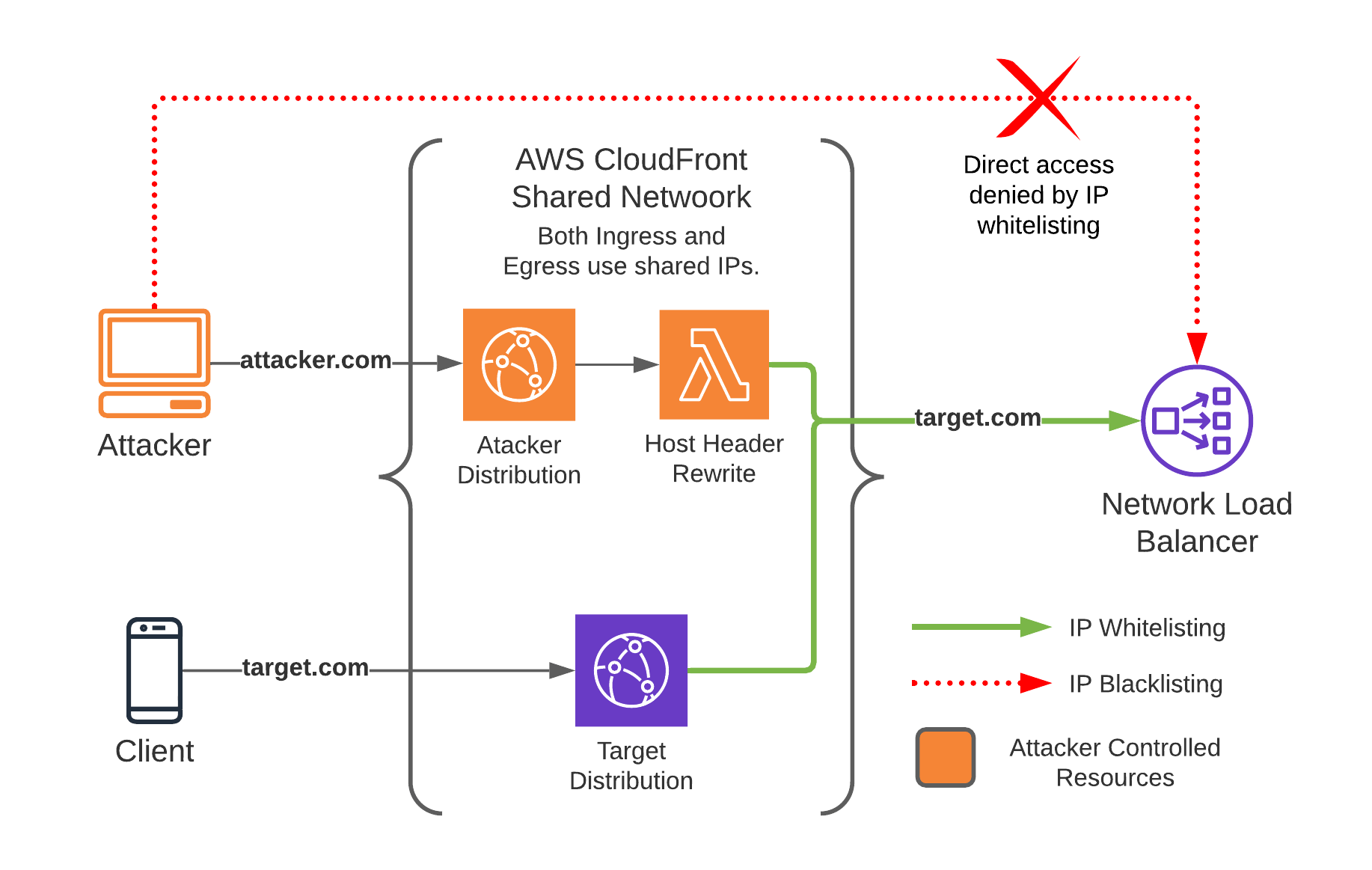 |
CDN Proxy |
| Create a copy of a targeted website with CDN and WAF restrictions disabled. |
|
|
 |
WinPwnage |
| UAC bypass, Elevate, Persistence methods. |
|
|
 |
catphish |
| Generate similar-looking domains for phishing attacks. |
|
|
 |
GCPBucketBrute |
| Enumerate Google Storage buckets, check the access and if they can be privilege escalated. |
|
|
 |
RedHunt-OS |
| Virtual machine for adversary emulation and threat hunting. |
|
|
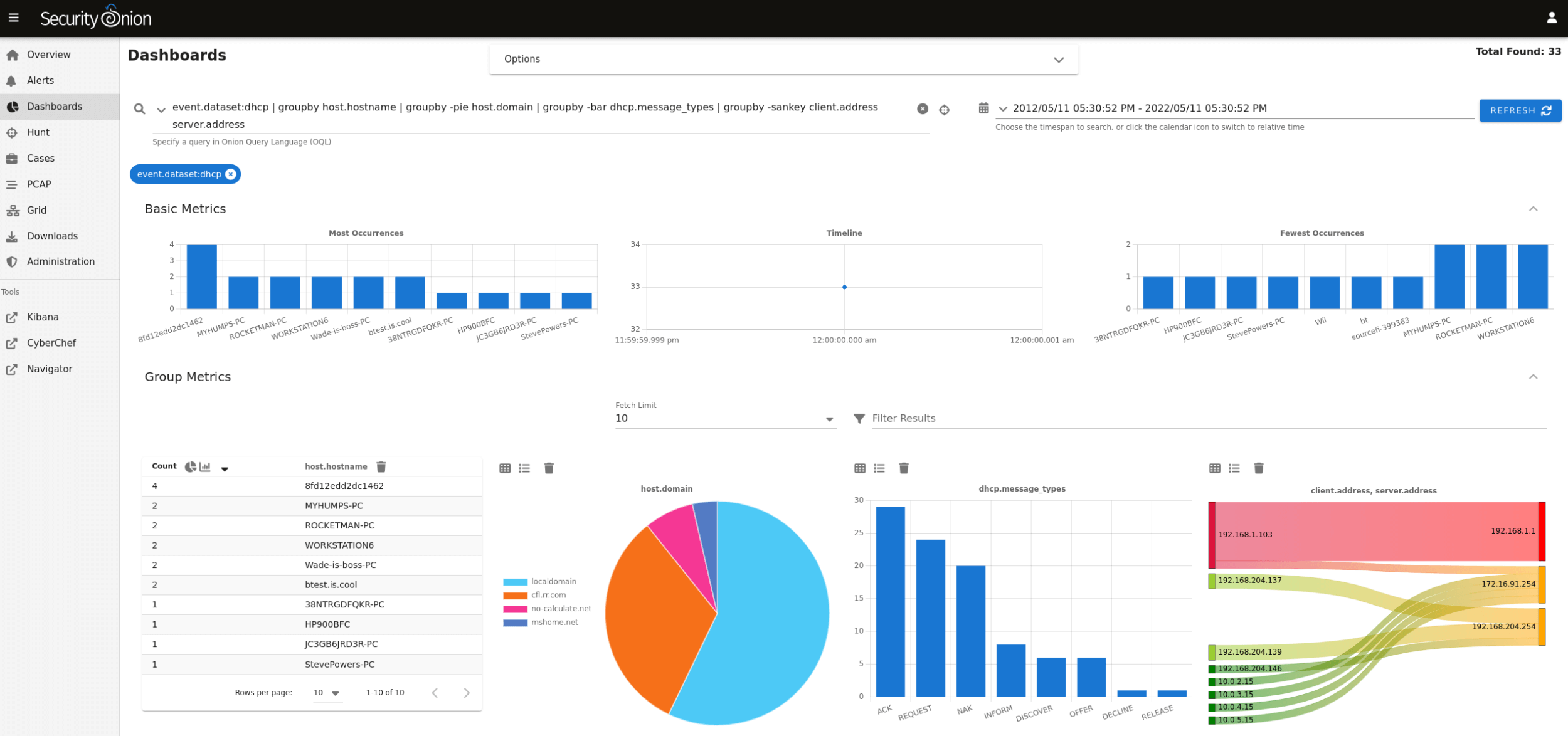 |
securityonion |
| Free and open platform for threat hunting, enterprise security monitoring, and log management. |
|
|
 |
litefuzz |
| A multi-platform fuzzer for poking at userland binaries and servers. |
|
|
 |
Vegile |
| Post exploitation tool to maintain some level of acces. |
|
|
 |
Microsploit |
| Quickly and easily create backdoor Office exploitation using module Metasploit packet. |
|
|
 |
FiercePhish |
| Full-fledged phishing framework to manage all phishing engagements. |
|
|
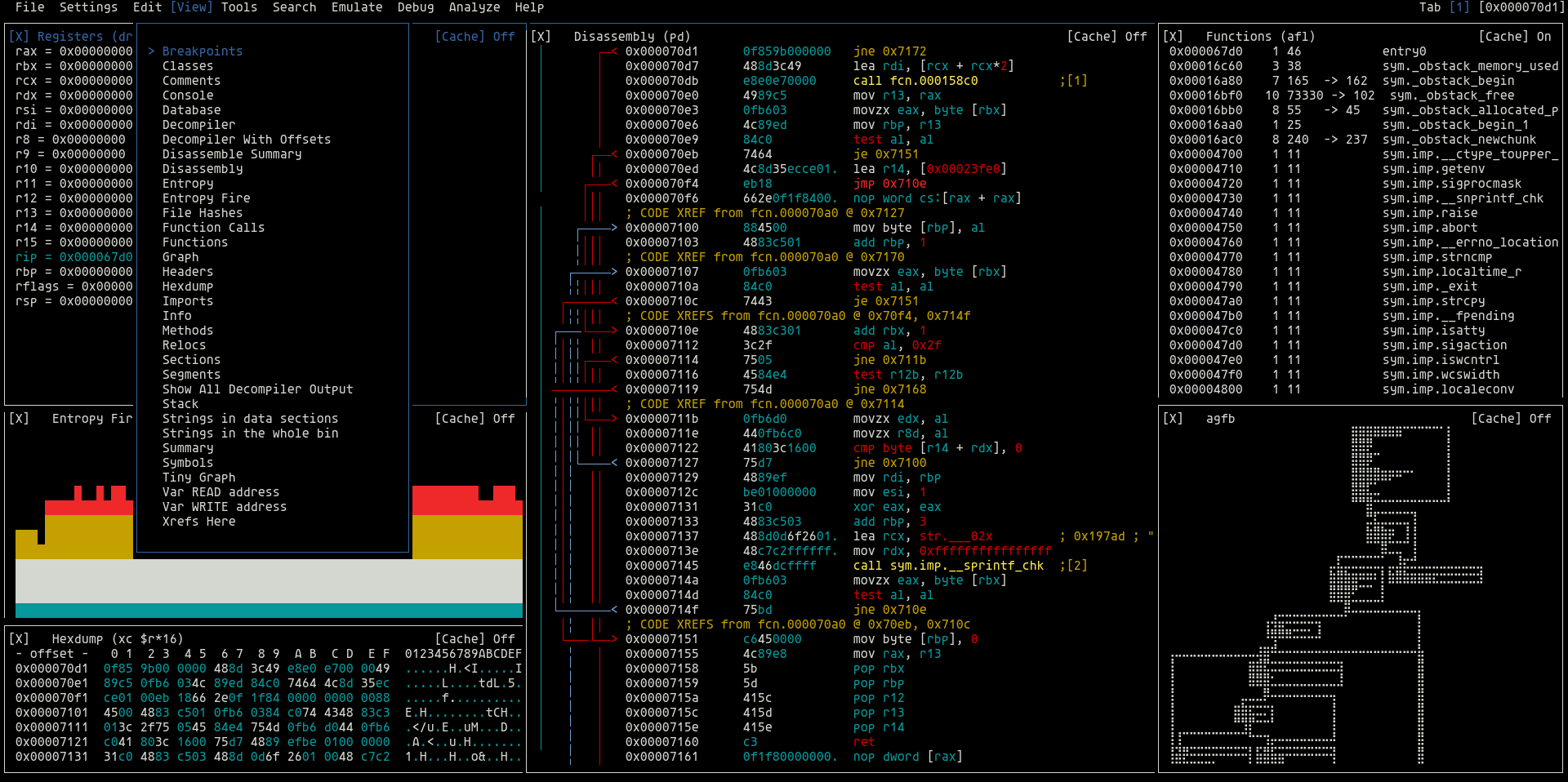 |
radare2 |
| UNIX-like reverse engineering framework and command-line toolset. |
|
|
|
|
 |
SMBetray |
| Attack clients through file content swapping and compromise any data passed in cleartext. |
|
|