Trishul
Burp Suite Extension to hunt for common vulnerabilities found in websites.
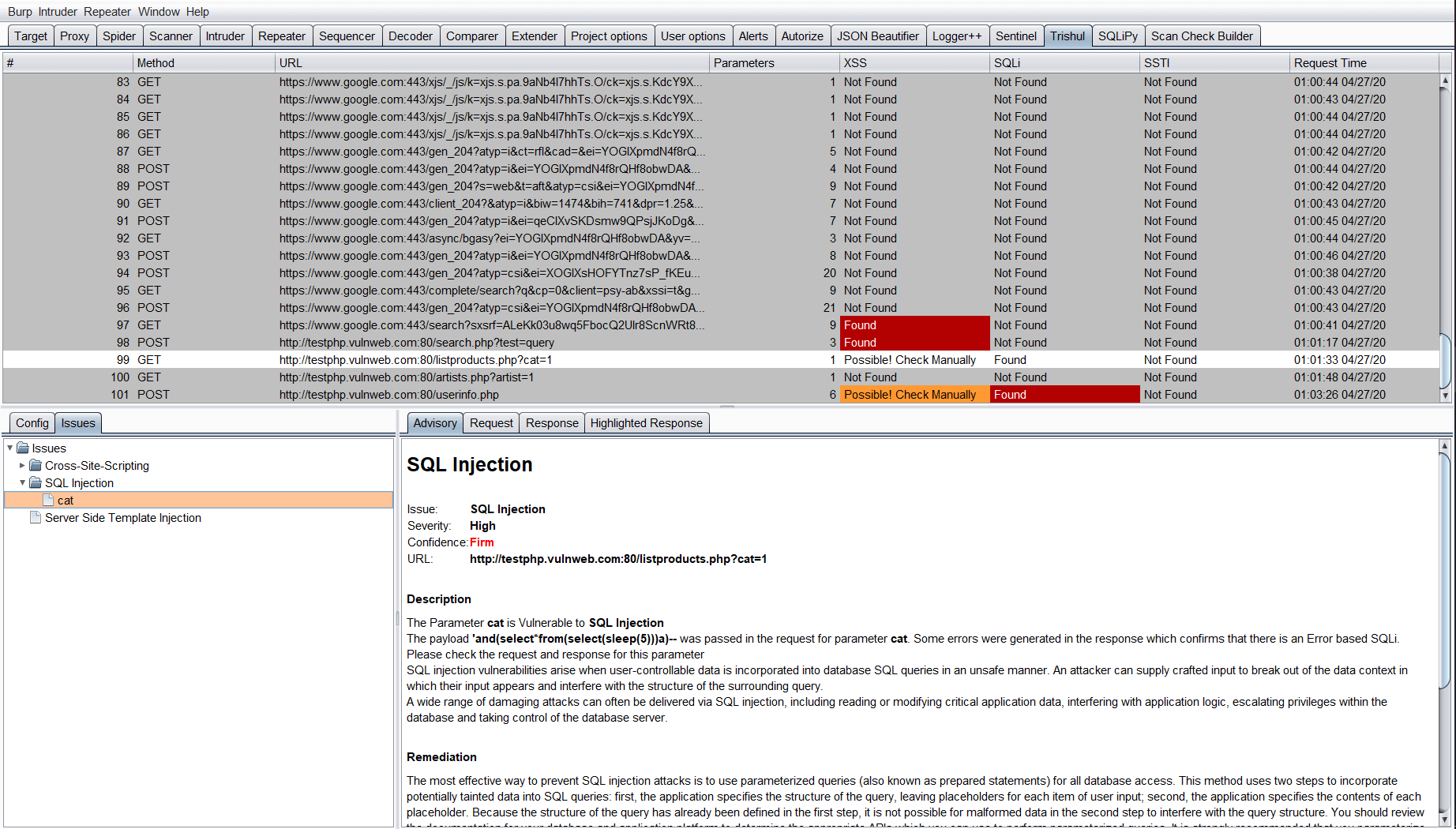
Trishul is an automated vulnerability finding Burp Extension. Built with Jython supports real-time vulnerability detection in multiple requests with user-friendly output. This tool was made to supplement testing where results have to be found in a limited amount of time. Currently, the tool supports finding of Cross-Site Scripting, SQL Injections and Server-Side Template Injections.
To detect vulnerabilities in requests, the requests are provided via the two ways:
- Send each request manually to Trishul
- Automatically test for all requests in a scope
For every result, Trishul displays one of the three options for each of the vulnerability tested:
- Found: The vulnerability was successfully detected for the Request parameters.
- Not Found: The vulnerability was not present in the Request parameters.
- Possible! Check Manually: The vulnerability maybe present, the tester has to reconfirm the finding.







