

SmuggleFuzz
A rapid HTTP downgrade smuggling scanner written in Go.
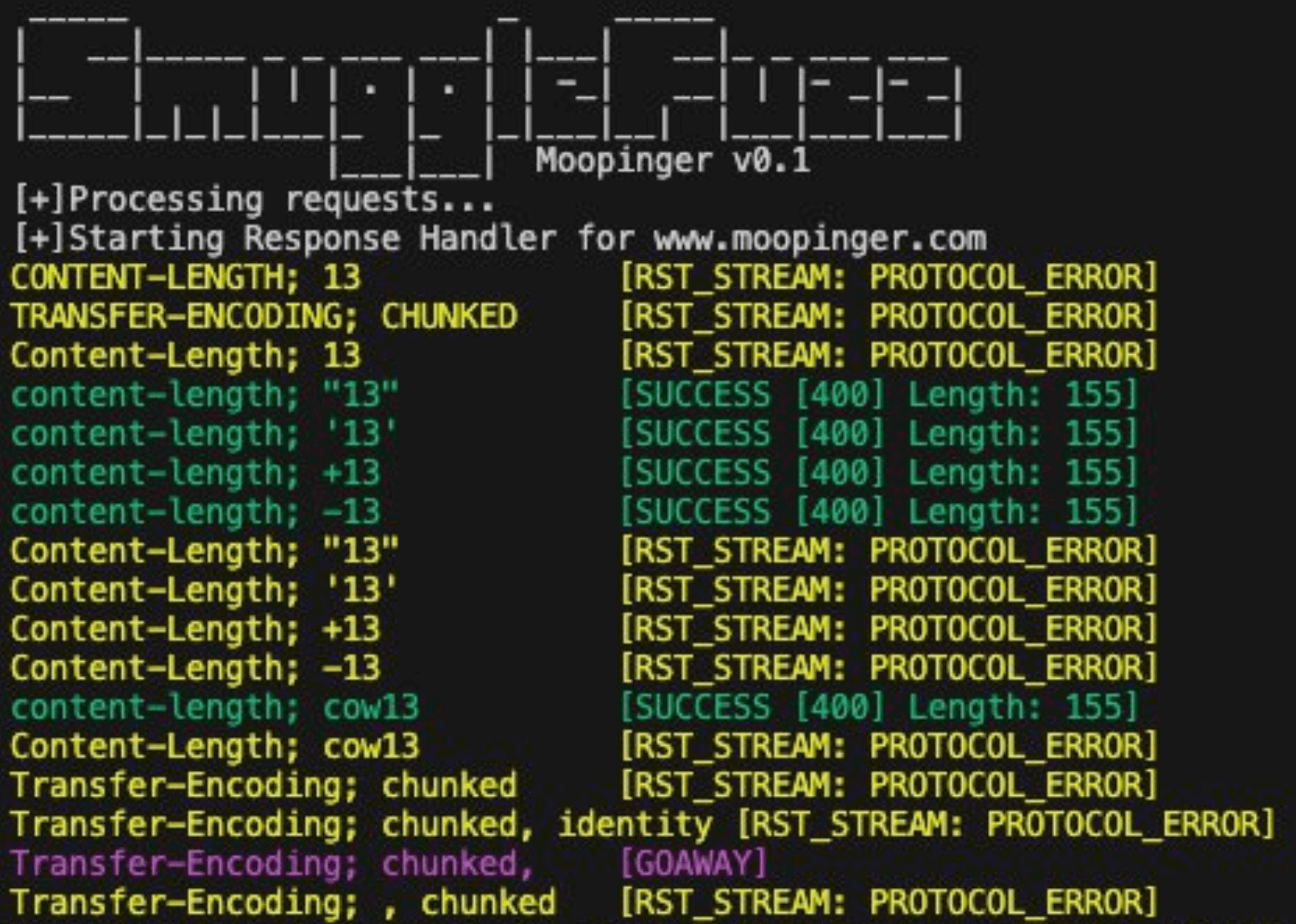
SmuggleFuzz, a configurable and rapid HTTP downgrade smuggling scanner. Empowering users with customizable gadget lists, it offers deeper insights into the reasons behind failed smuggling attacks. I am confident that numerous HTTP downgrade-based smuggling vulnerabilities remain undiscovered. Unfortunately, many individuals cease their exploration after a cursory scan. By using SmuggleFuzz, you can uncover smuggling vulnerabilities that others may overlook.
SmuggleFuzz allows users complete control over requests through custom wordlists. These lists have a basic structure, which should be followed for optimal request handling. For instance, headers and their values are split using a semicolon and a space (; ) instead of the usual colon, facilitating the inclusion of colon values in smuggling requests. This also opens up possibilities for various mutations and creative approaches.
The tool includes a ready-to-use list of 125 smuggling gadgets, though there's always scope for expansion.
Users can run scans with custom wordlists.







