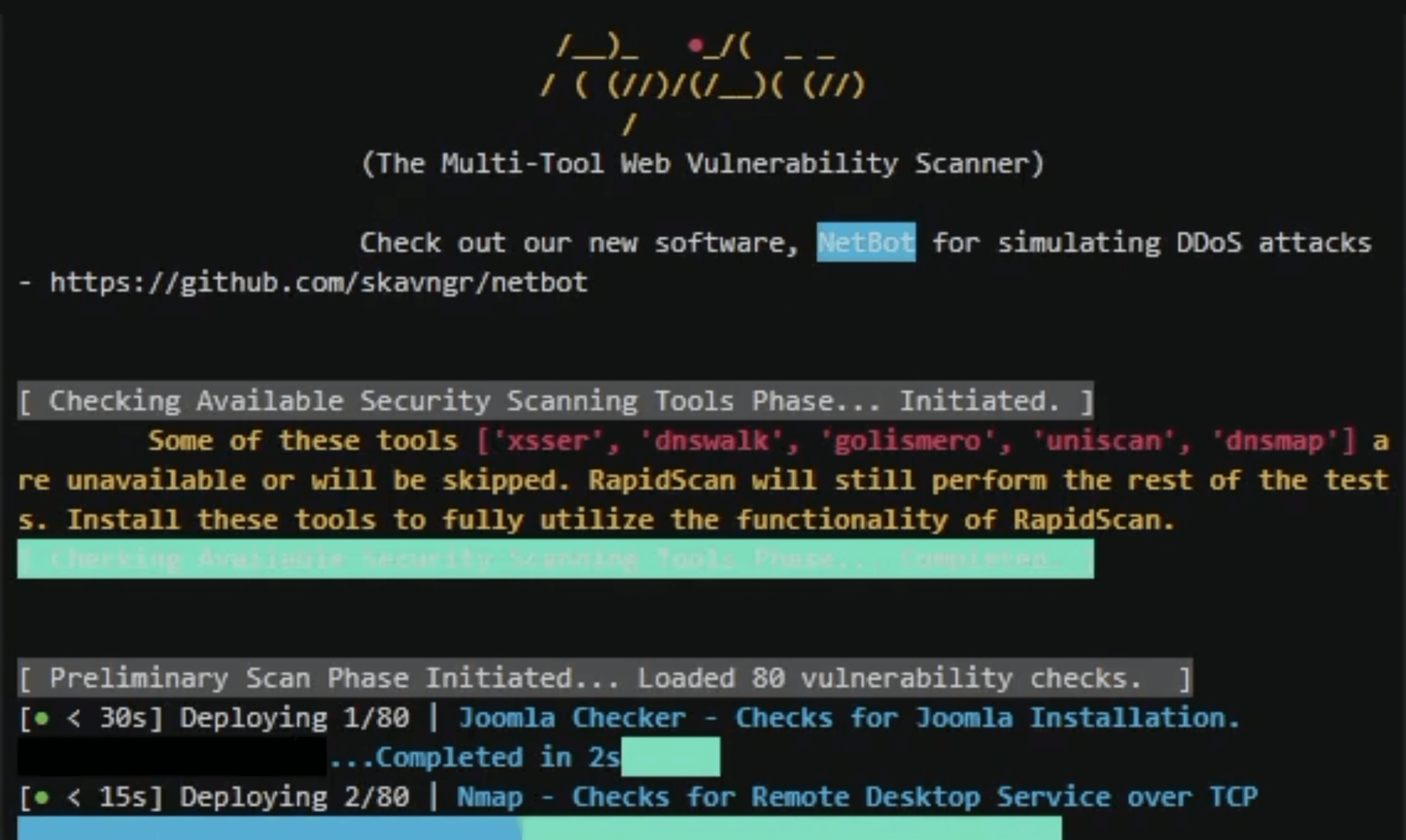

Rapidscan
The multi tool web vulnerability scanner.
Features:
- one-step installation.
- executes a multitude of security scanning tools, does other custom coded checks and prints the results spontaneously.
- some of the tools include nmap, dnsrecon, wafw00f, uniscan, sslyze, fierce, lbd, theharvester, amass, nikto etc executes under one entity.
- saves a lot of time, indeed a lot time!
- checks for same vulnerabilities with multiple tools to help you zero-in on false positives effectively.
- extremely light-weight and not process intensive.
- legends to help you understand which tests may take longer time, so you can Ctrl+C to skip if needed.
- association with OWASP Top 10 & CWE 25 on the list of vulnerabilities discovered. (under development)
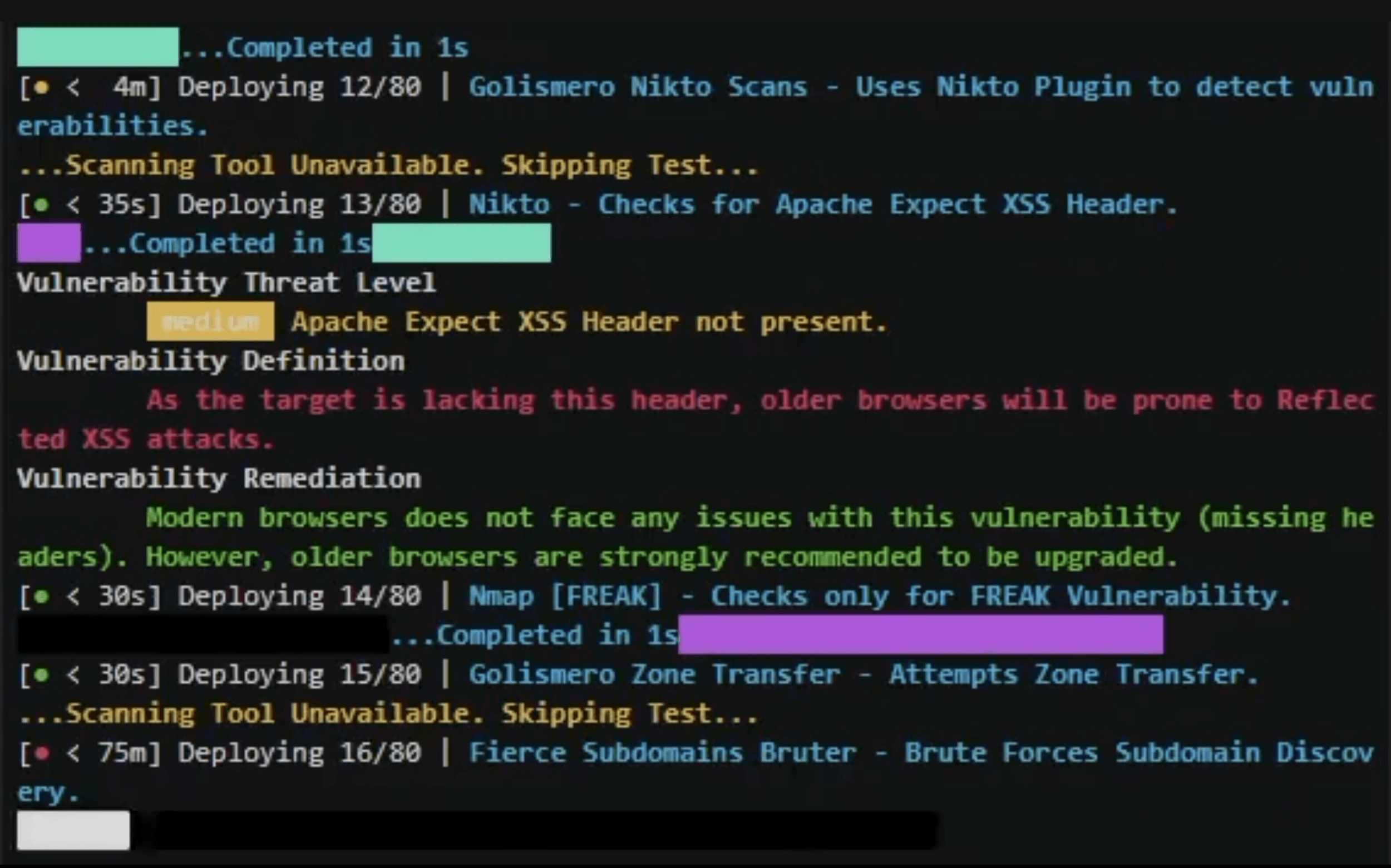
- critical, high, medium, low and informational classification of vulnerabilities.
- vulnerability definitions guides you what the vulnerability actually is and the threat it can pose.
- remediation tells you how to plug/fix the found vulnerability.
- executive summary gives you an overall context of the scan performed with critical, high, low and informational issues discovered.
- artificial intelligence to deploy tools automatically depending upon the issues found. for eg; automates the launch of wpscan and plecost tools when a wordpress installation is found. (under development)
- detailed comprehensive report in a portable document format (*.pdf) with complete details of the scans and tools used. (under development)
- on the run metasploit auxilliary modules to discover more vulnerabilities. (under development)
Vulnerability checks:
- DNS/HTTP Load Balancers & Web Application Firewalls.
- Checks for Joomla, WordPress, and Drupal
- SSL-related Vulnerabilities (HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling).
- Commonly Opened Ports.
- DNS Zone Transfers using multiple tools (Fierce, DNSWalk, DNSRecon, DNSEnum).
- Sub-Domains Brute Forcing (DNSMap, amass, nikto)
- Open Directory/File Brute Forcing.
- Shallow XSS, SQLi, and BSQLi Banners.
- Slow-Loris DoS Attack, LFI (Local File Inclusion), RFI (Remote File Inclusion) & RCE (Remote Code Execution).







