

PINCE
Reverse engineering tool for linux games.
PINCE is a front-end/reverse engineering tool for the GNU Project Debugger (GDB), focused on games. However, it can be used for any reverse-engineering related stuff. PINCE is an abbreviation for "PINCE is not Cheat Engine".
Features:
- Memory scanning: PINCE uses a specialized fork of libscanmem to scan the memory efficiently
- Pointer scanning: PINCE uses PointerScanner-X to scan pointers efficiently
- Background Execution: PINCE uses background execution by default, allowing users to run GDB commands while process is running
- Variable Inspection & Modification: cheatengine-like value type support, symbol recognition, automatic variable allocation, dynamic address table, smart casting, variable locking
- Memory View: assembler, dissect code, bookmarking, modify on the fly, opcode search
- Debugging: chained breakpoints, watchpoint tracking, breakpoint tracking, tracing, collision detection
- Code Injection: run-time injection
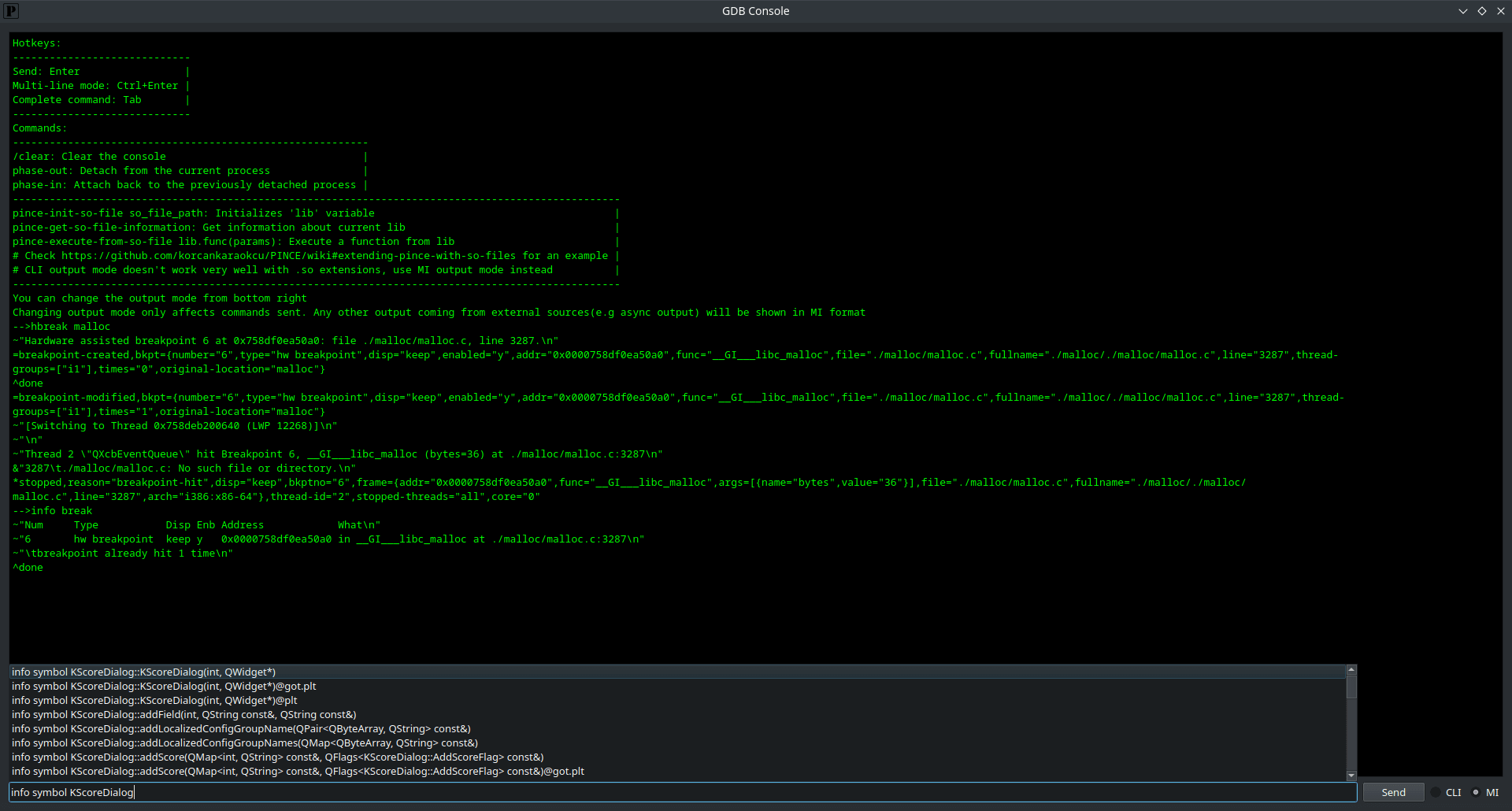
- GDB Console: you can use the GDB Console to interact with GDB, it's on the top right in main window
- libpince: PINCE provides a reusable python library
- Extendable with .so files at runtime







