
Inspeckage
Android package inspector.
Inspeckage is a tool developed to offer dynamic analysis of Android applications. By applying hooks to functions of the Android API, Inspeckage will help you understand what an Android application is doing at runtime.
- Information gathering:
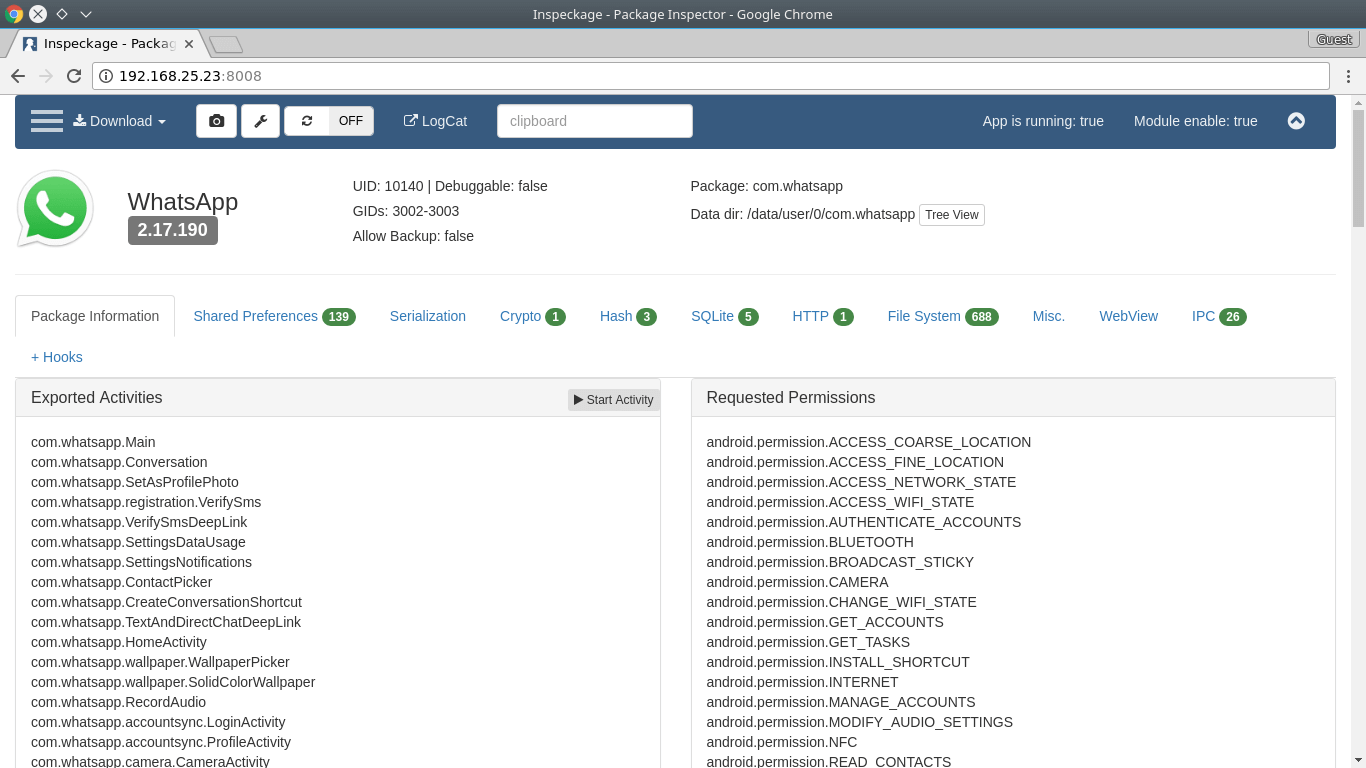
Requested Permissions
App Permissions
Shared Libraries
Exported and Non-exported Activities, Content Providers,Broadcast Receivers and Services
Check if the app is debuggable or not
Version, UID and GIDs
etc.
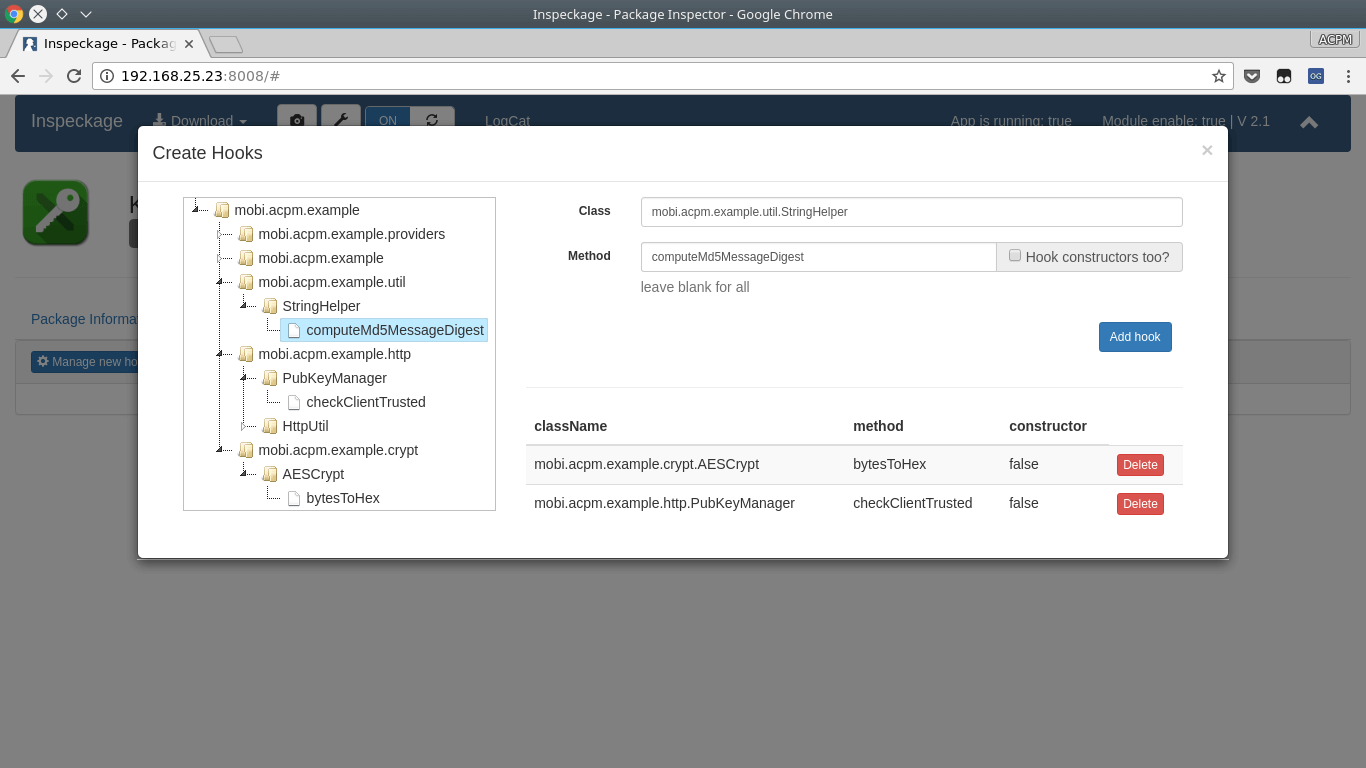
- Hooks, with the hooks we can see what the application is doing in real time:
Shared Preferences (log and file)
Serialization
Crypto
Hashes
SQLite
HTTP (an HTTP proxy tool is still the best alternative)
File System
Miscellaneous (Clipboard, URL.Parse())
WebView
IPC
Hooks (add new hooks dynamically)
- Actions, with Xposed it's possible to perform actions such as start a unexported activity and much else:
Start any activity (exported and unexported)
Call any provider (exported and unexported)
Disable FLAG_SECURE
SSL uncheck (bypass certificate pinning - JSSE, Apache and okhttp3)
Start, stop and restart the application
Replace params and return value (+Hooks tab).
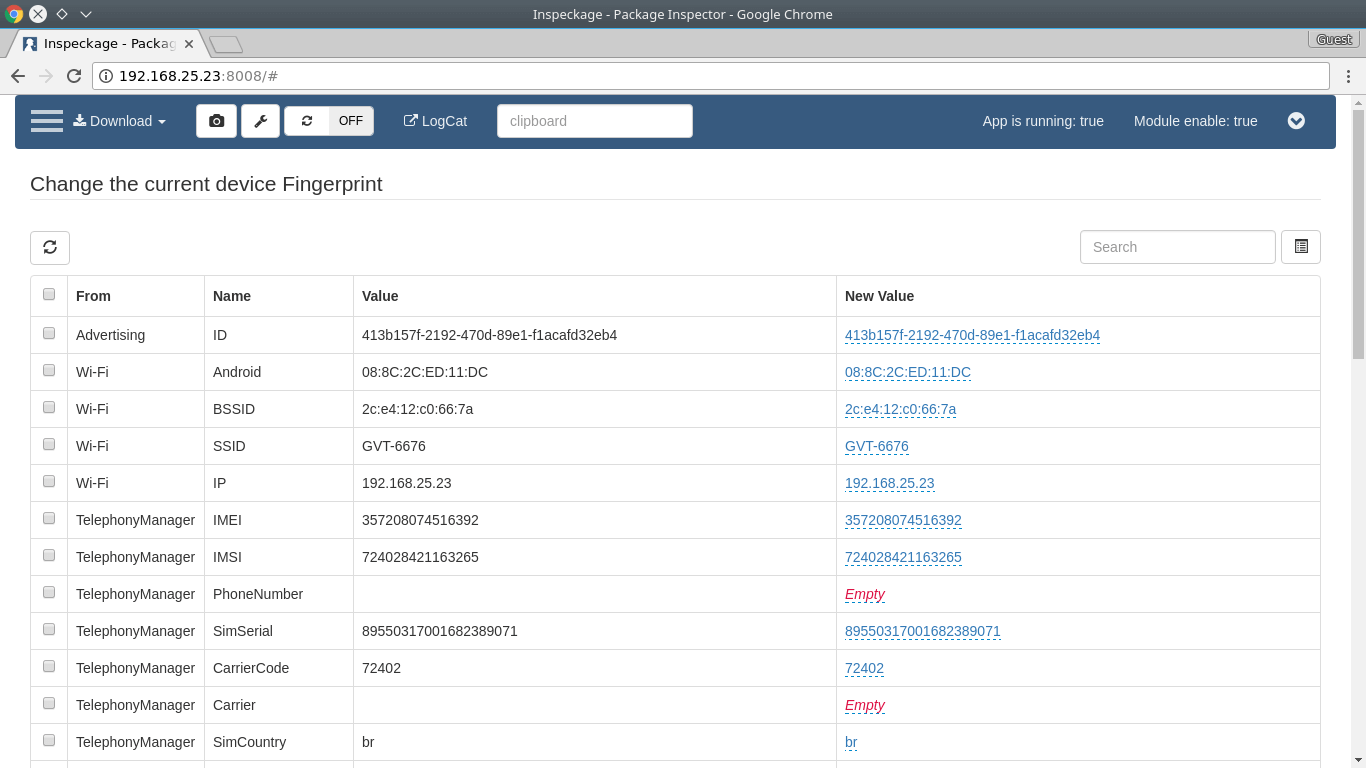
- Fingerprint:
Device fingerprint - advertising id, MAC address, IMEI, release, brand, build mode...
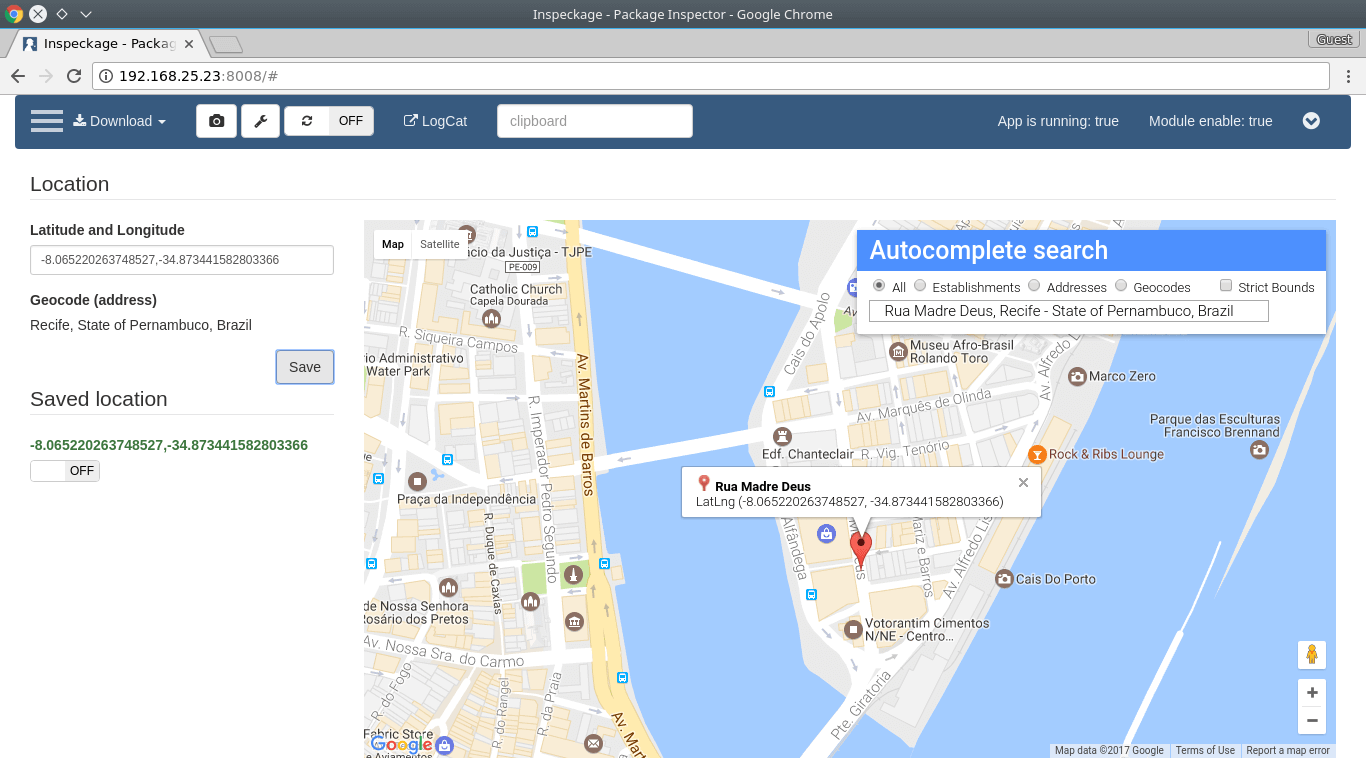
- Location:
Change GPS location (without use "Mock location" functionality)
- Extras:
APK Download
View the app's directory tree
Download the app's files
Download the output generated by hooks in text file format
Take a screen capture
Send text to android clipboard.
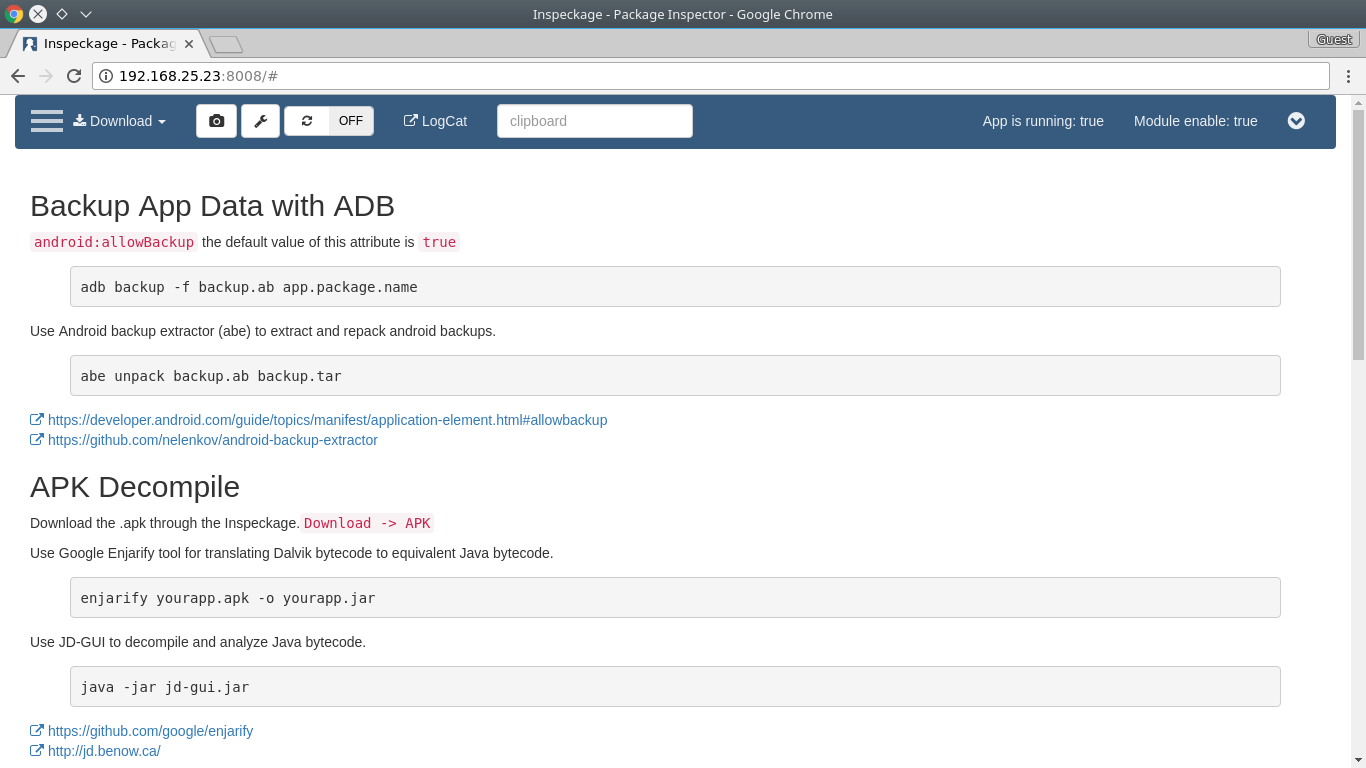
Tips - some howto/guide
- Configuration, even though our tool has some hooks to the HTTP libraries, using an external proxy tool is still the best option to analyze the app's traffic:
Add a proxy to the target app
Enable and disable proxy
Add entries in the arp table.
- Logcat:
Logcat.html page. A experimental page with websocket to show some information from the logcat.







