graftcp
A flexible tool for redirecting a given program's TCP traffic to SOCKS5 or HTTP proxy.
graftcp can redirect the TCP connection made by the given program [application, script, shell, etc.] to SOCKS5 or HTTP proxy.
Compared with tsocks, proxychains or proxychains-ng, graftcp is not using the LD_PRELOAD trick which only work for dynamically linked programs, e.g., applications built by Go can not be hook by proxychains-ng. graftcp can trace or modify any given program's connect by ptrace(2), so it is workable for any program.
To achieve the goal of redirecting the TCP connection of a app to another destination address and the app itself is not aware of it, these conditions are probably required:
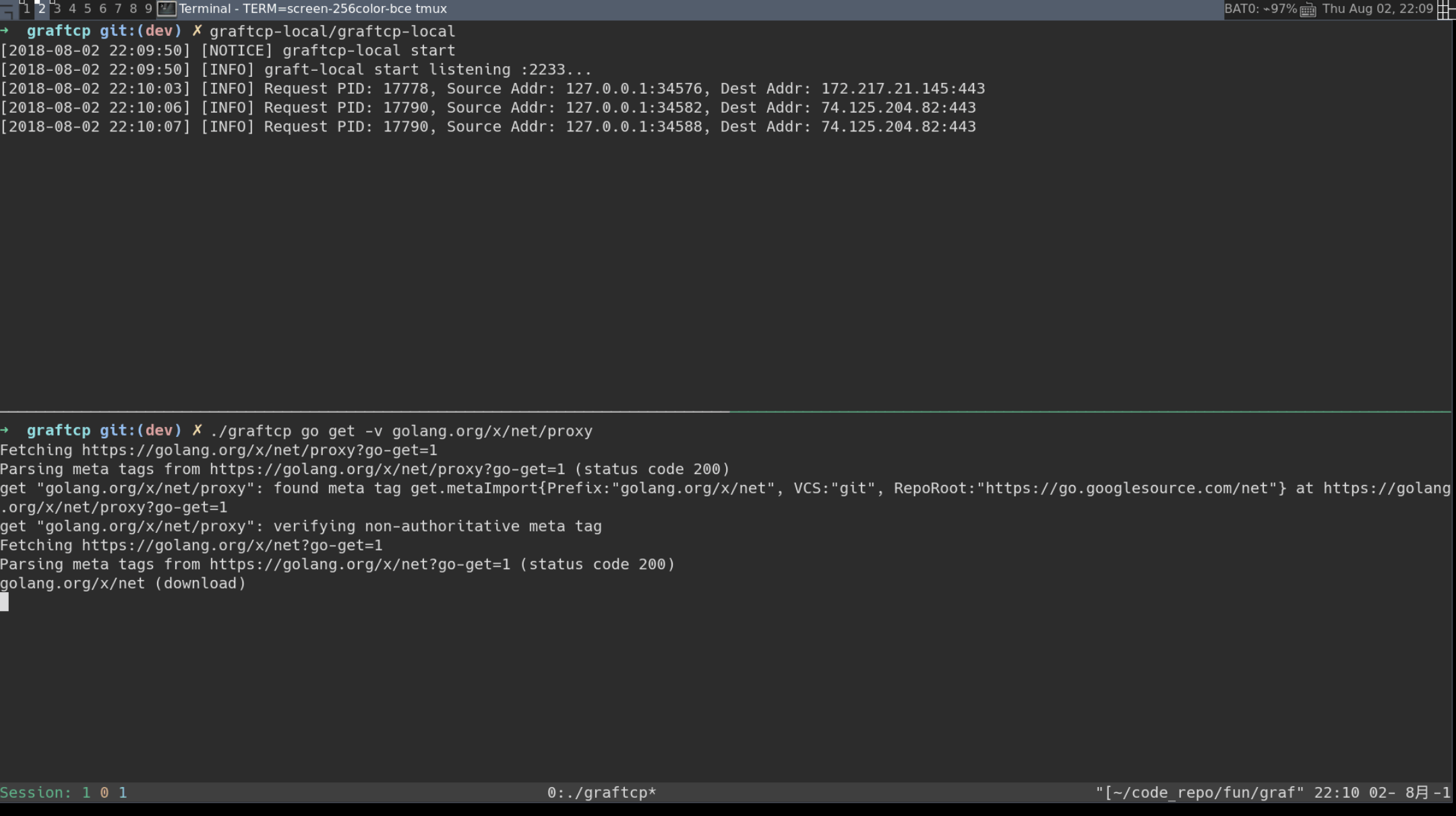
- fork(2) a new process and trace it using ptrace(2), execve(2) to run the app. Every connect(2) syscall will be intercepted, then get the destination address argument and send it to graftcp-local via pipe.
- kodify the destination address argument of connect(2) to graftcp-local's address, and restart the stopped syscall. After the syscall returns successfully, the app thought it has connected the original destination address, but in fact it is connected to the graftcp-local, so we named it "graft".
- graftcp-local establish a SOCKS5 connection based on the information of app's original destination address, then redirect the requests from the app to the SOCKS5 proxy.







