
CORStest
A simple CORS misconfiguration scanner.
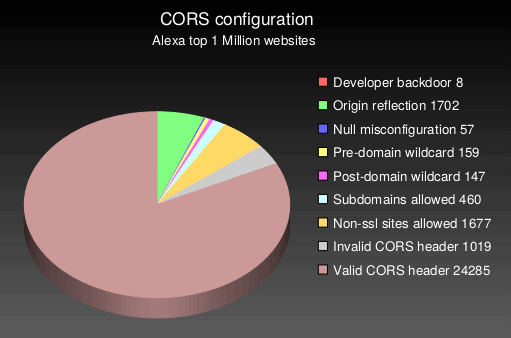
CORStest is a quick & dirty Python 3 tool to find Cross-Origin Resource Sharing (CORS) misconfigurations. It takes a text file as input which may contain a list of domain names or URLs. Currently, the following potential vulnerabilities are detected by sending a certain Origin request header and checking for the Access-Control-Allow-Origin response header:
- Developer backdoor
- Origin reflection
- Null misconfiguration
- Pre-domain wildcard
- Post-domain wildcard
- Subdomains allowed
- Non-ssl sites allowed
- Invalid CORS header







