

BruteShark
Network forensic analysis tool that performs deep processing and inspection of network traffic.
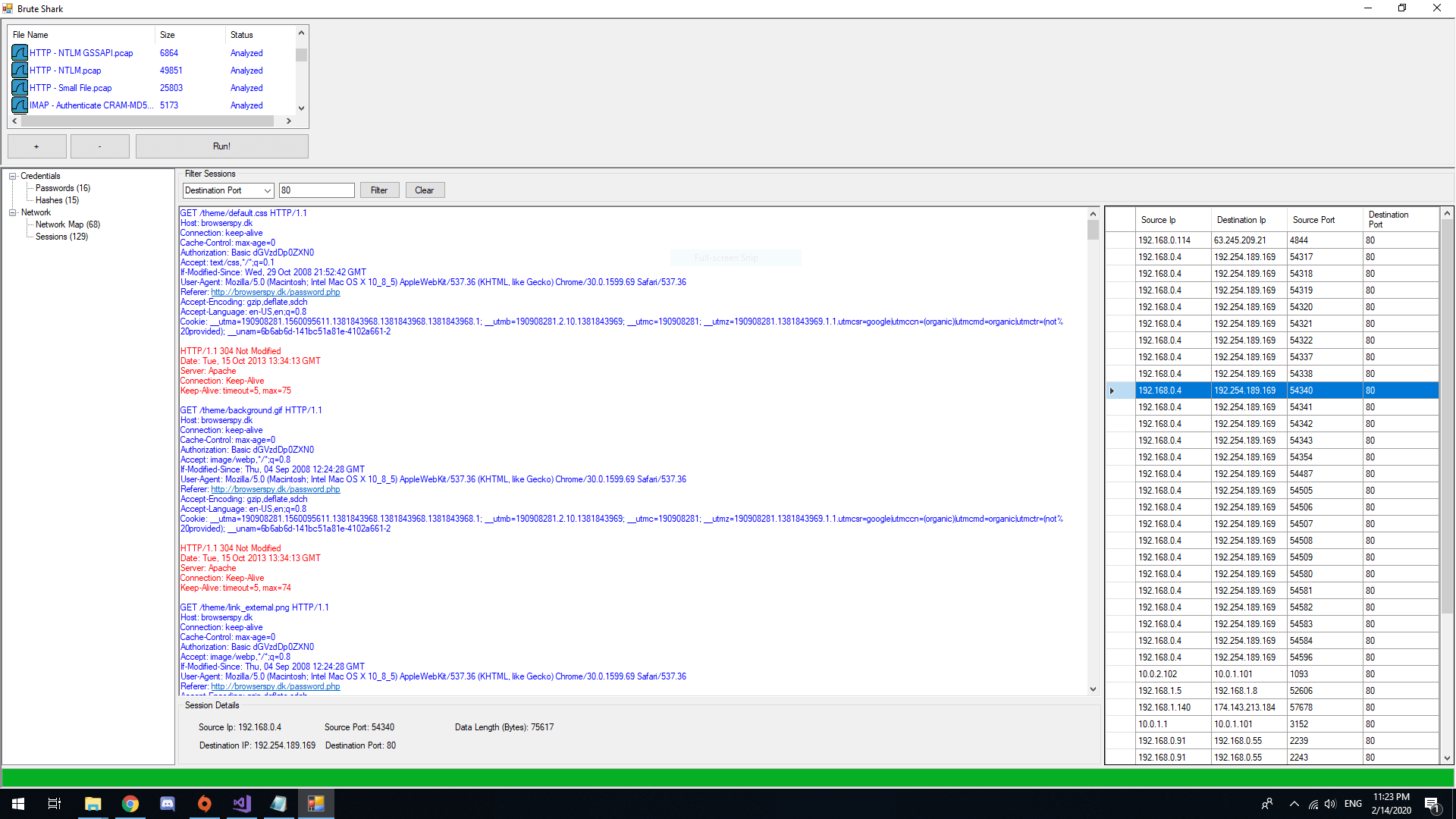
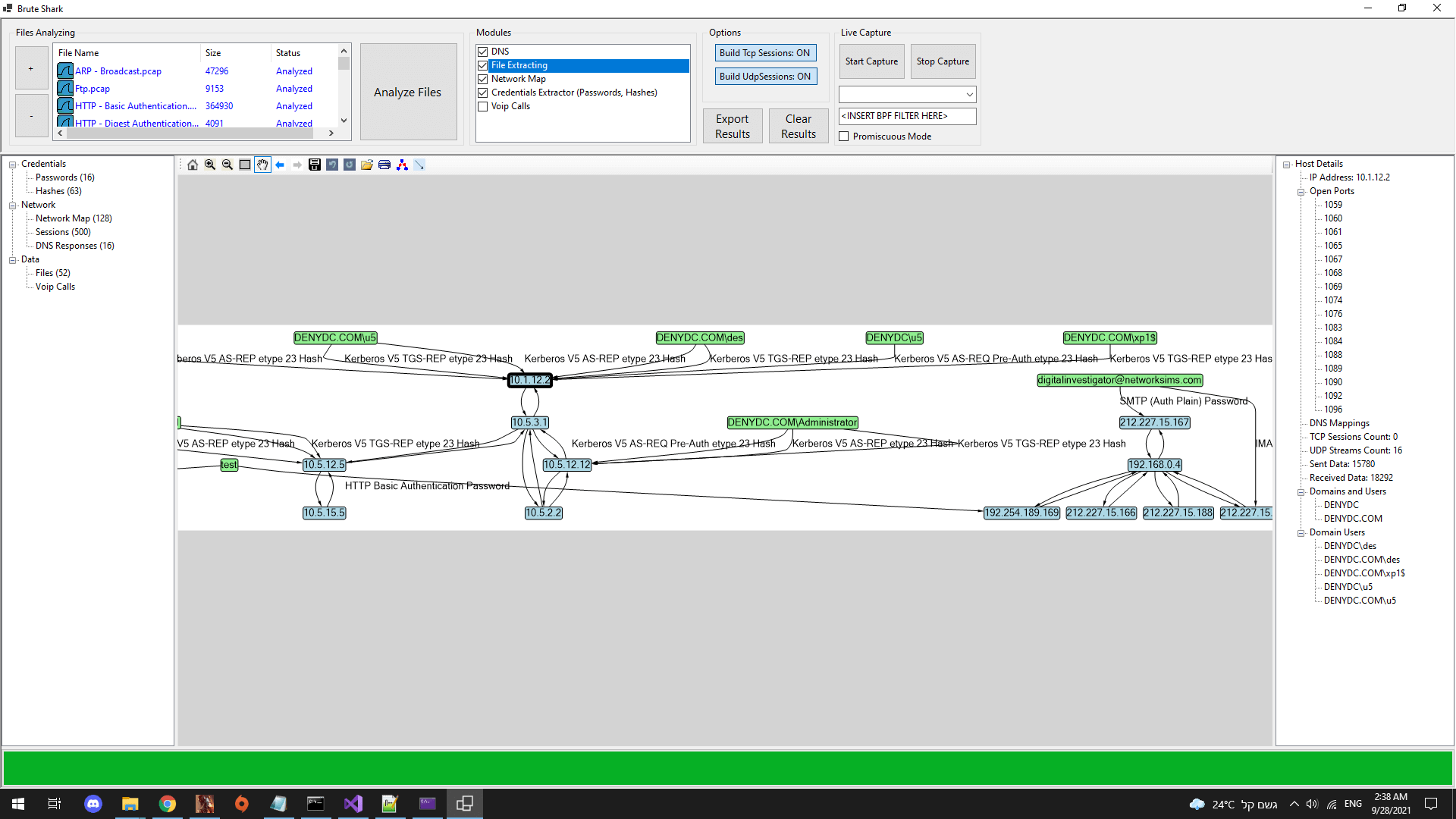
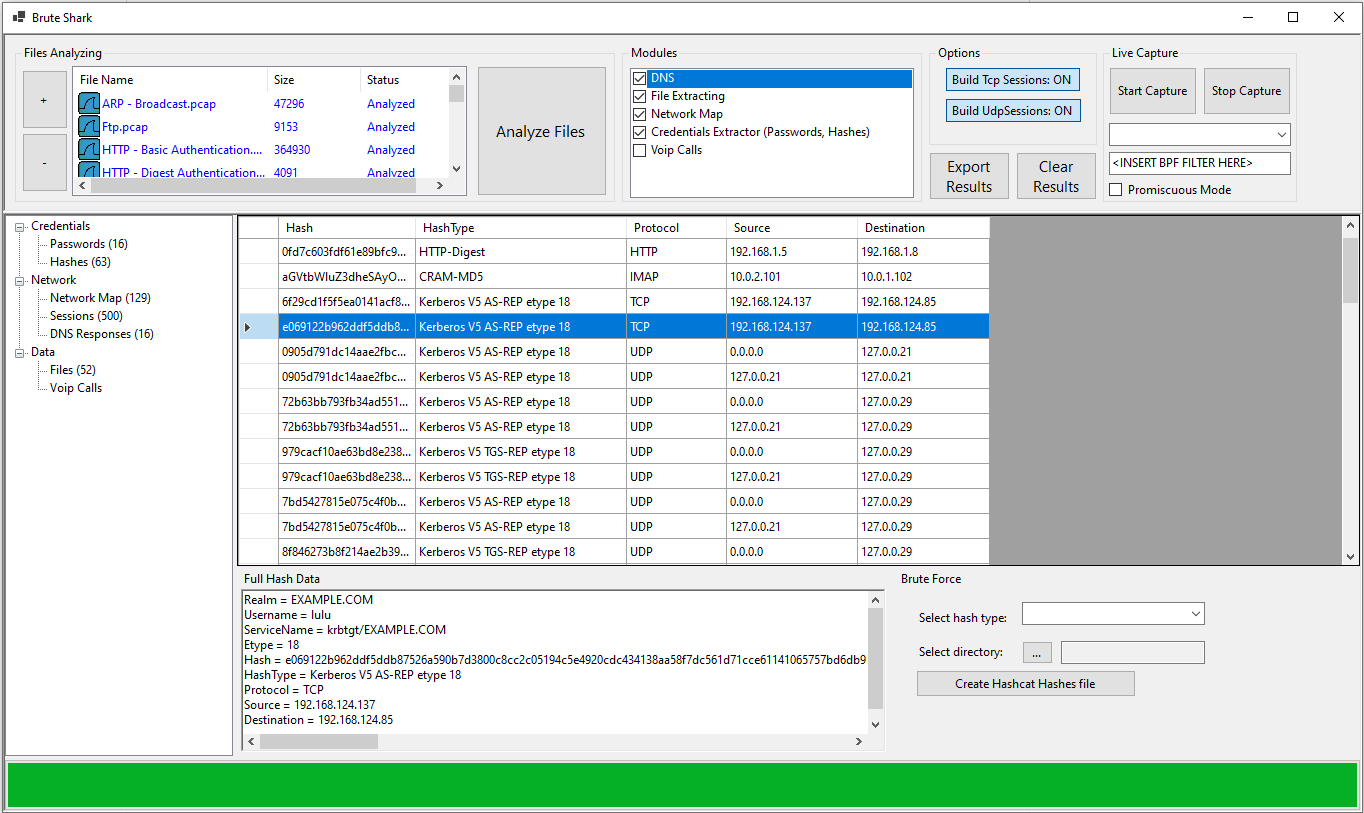
It includes: password extracting, building a network map, reconstruct TCP sessions, extract hashes of encrypted passwords and even convert them to a Hashcat format in order to perform an offline Brute Force attack.
The main goal of the project is to provide solution to security researchers and network administrators with the task of network traffic analysis while they try to identify weaknesses that can be used by a potential attacker to gain access to critical points on the network.
Two BruteShark versions are available, A GUI based application (Windows) and a Command Line Interface tool (Windows and Linux).
The various projects in the solution can also be used independently as infrastructure for analyzing network traffic on Linux or Windows machines. For further details see the Architecture section.
What it can do:
- Extracting and encoding usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP...)
- Extract authentication hashes and crack them using Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
- Build visual network diagram (Network nodes, Open Ports, Domain Users)
- Extract DNS queries
- Reconstruct all TCP & UDP Sessions
- File Carving
- Extract Voip calls (SIP, RTP)







